Data spaces in Superset
To configure the data space model of the platform in Superset, users are assigned data space-specific roles in Superset. This ensures that data access and manipulation are tightly controlled through role-based permissions, allowing users to interact only with the data and visualizations relevant to data spaces they have access to.
Apache Superset manages access to data visualizations, dashboards, and data sources using Roles, Users, Permissions, Data sources, and Dashboards. In the platform, each Data space represents a thematic area containing specific data and visualizations. In Superset, this concept is implemented by creating roles and permissions that control access to resources (such as dashboards and charts) within a data space.
How the Platform's Data space Concept Maps to Superset
- User: A person or system entity that accesses Superset to view or manage dashboards and data sources. Users are assigned roles that define what actions they can perform within a data space.
- Role: A collection of permissions in Superset that defines what a user can do within a specific data space. For example, a role might allow a user to view, edit, or manage dashboards and data sources within a certain thematic area (data space).
- Permission: A specific right or authorization to perform actions such as viewing, editing, or deleting resources in Superset. Permissions can be configured for specific data sources or dashboards, allowing fine-grained control over what users can do.
- Data source: A collection of data (e.g., tables, databases, or datasets) that users access to create visualizations and dashboards. Data sources are part of a data space and define the scope of the data available for that data space.
- Dashboard: A visual representation of data from a specific data space. Dashboards allow users to explore, analyze, and interact with data from the associated data sources. In Superset, Roles and Permissions are used to manage user access to data sources and dashboards. For each Data space, we implement a custom set of roles and permissions to enforce the platform’s data space concept. This ensures that users are given access only to the specific resources within a data space that they are allowed to interact with.
Example for Keycloak and Superset
The following settings describe the data spaces named "baumkataster" and "denkmalschutz" defined in Keycloak and Superset:
- Keycloak "Groups":
- Group for data space "baumkataster":
baumkataster - Group for data space "denkmalschutz":
denkmalschutz - N.B.: When creating a group, two key-value pairs must be assigned as attributes, namely "service":"true" and "tenant":"true"
- Group for data space "baumkataster":
- Keycloak user "Max Mustermann" (
max@mustermann.de)- User-Group-Assignments:
baumkataster,denkmalschutz
- User-Group-Assignments:
- Superset roles:
baumkataster,denkmalschutz
If Max requests a resource from Superset and therefore logs into Superset (via the Keycloak),
- Keycloak sends an access_token: (user:
max@mustermann.de, groups: [baumkataster,denkmalschutz]) - Superset creates a User:
max@mustermann.de(if not already existing) - Based on the groups, the user is assigned the corresponding roles in Superset (
baumkataster,denkmalschutz) - Permissions are manually assigned to roles in Superset
Mapping illustrated
The mapping is illustrated in the following image, using matching colors for corresponding objects.
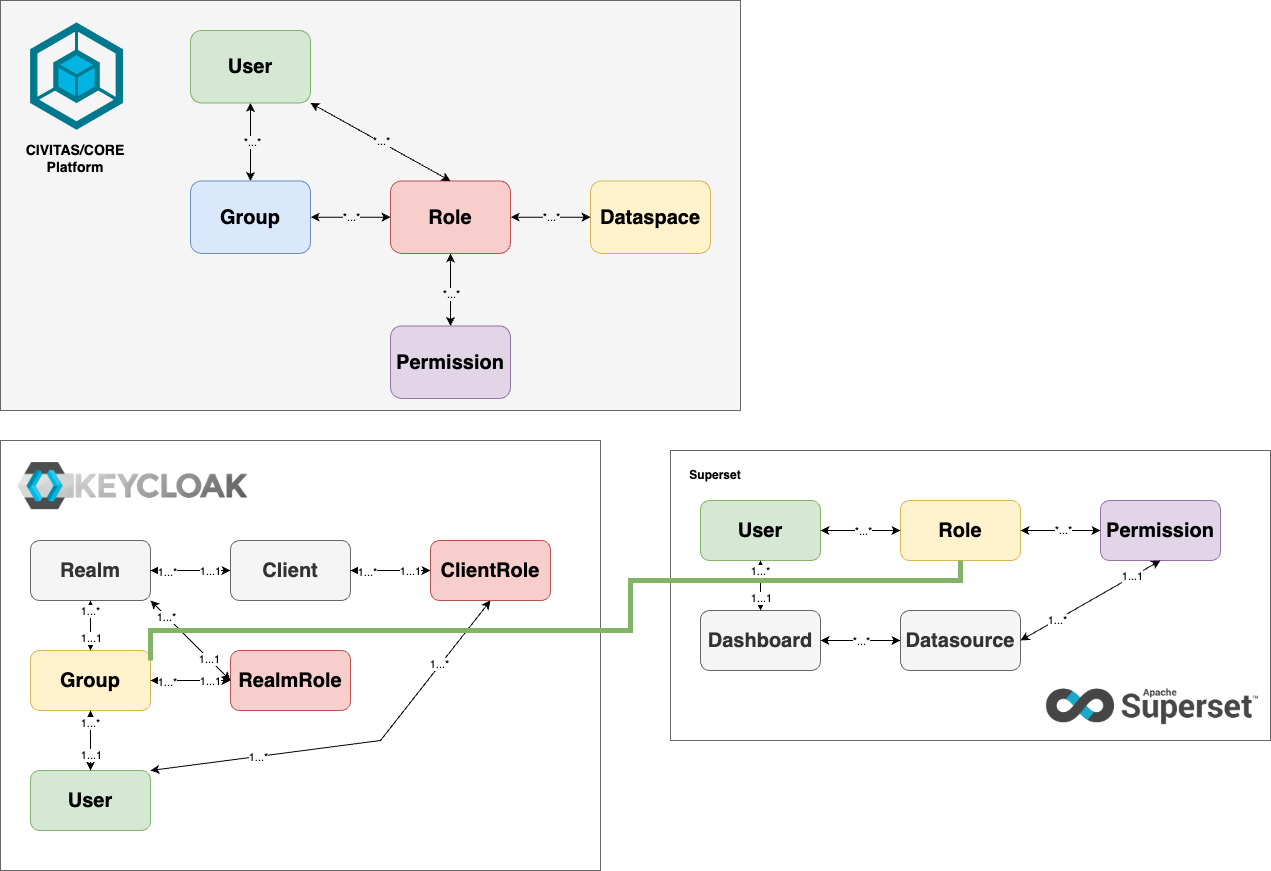
Setting Up Data spaces in Superset
To configure the platform’s data space concept in Superset, assign permissions to each data space's role. Roles must have specific permissions to allow actions on resources (like dashboards or data sources). Permissions may vary depending on the role and the data space.
For detailed instructions on how to configure roles, define permissions, and assign them to users in Superset, refer to the Admin Guide.