Data spaces in GeoServer
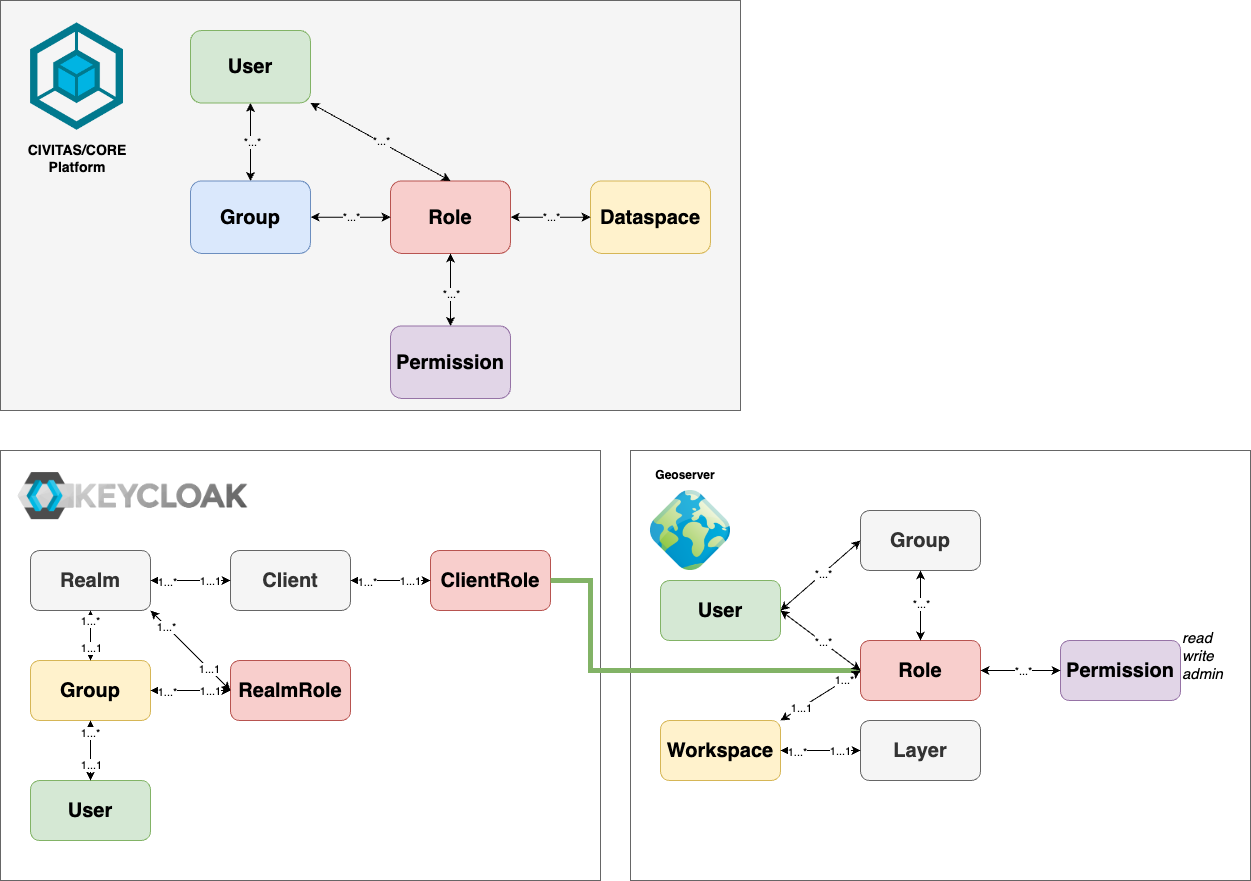
To configure the data space model of the platform in GeoServer, users are assigned to data space-specific roles in Keycloak. This ensures that data access and manipulation are tightly controlled through role-based permissions, allowing users to interact only with the geo-spatial content relevant to data spaces they have access to. The GeoServer manages access to geo-spatial content using Roles, Users, Permissions, and Groups.
How the Platform's Data space Concept Maps to GeoServer
For each data space, we implement our own set of roles which get permissions on geo-spatial data (Layers, Layer-groups) granted by assigning the corresponding permissions to the role in GeoServer.
- Layers: Layers are the finest level where permissions to roles in the GeoServer can be granted. On this level, you can specify Read, Write or Administrative Access individually to each layer. Additionally, Layers are assigned to workspaces in GeoServer and inherit the permissions from there, if no individual configuration is done on layer level.
- Layer-groups: Layer-groups are from the security perspective special layer types. Layer-groups are managed in the same way as layers.
- Permission: Permissions in GeoServer (standard, without plugins) can be assigned in three levels: read, write and admin. Read and Write grant only access to existing Layers (using them). Admin permissions grant the right to manage a layer.
- Groups GeoServer allows working with groups within the platform. These are not used for the CIVITAS/CORE Platform.
- Workspaces Workspaces in GeoServer are a hierarchical structure above many GeoServer entities like Layers and Layer-groups. They are only used to structure the content. In CIVITAS/CORE we use them to group all Entities of one data space. This grouping enables permissions and role assignments to be set at the workspace level, with inheritance to assigned entities.
Example for Keycloak and GeoServer
The following settings describe the data spaces named "baumkataster" and "denkmalschutz" defined in Keycloak and GeoServer:
- Keycloak client "geo-data":
- Roles for data space "baumkataster":
baumkataster - Roles for data space "denkmalschutz":
denkmalschutz
- Roles for data space "baumkataster":
- Keycloak client scopes "api:read", "api:write" and "api:delete":
- Roles
baumkatasteranddenkmalschutzare added to "api:read", "api:write" and "api:delete"
- Roles
- Keycloak user "Max Mustermann" (
max@mustermann.de)- User-Role-Assignments:
baumkataster,denkmalschutz
- User-Role-Assignments:
- GeoServer workspaces:
baumkataster,denkmalschutz - GeoServer Data Security Rules for each workspace
baumkataster,denkmalschutz:- Role
baumkatasteris in Selected Roles in the Data Security Rule for Workspacebaumkataster(unclick "Grant access to any roles") - Role
denkmalschutzis in Selected Roles in the Data Security Rule for Workspacedenkmalschutz(unclick "Grant access to any roles")
- Role
If Max requests a resource from GeoServer and therefore logs into GeoServer (via the Keycloak),
- Keycloak sends an access_token: (user:
max@mustermann.de, roles: [baumkataster,denkmalschutz]) - GeoServer creates a User:
max@mustermann.de(if not already existing) - GeoServer creates the roles: (
baumkataster,denkmalschutz) - Manually in GeoServer, the permissions Read, Write and Admin are assigned to the roles
Mapping illustrated
The mapping is illustrated in the following image, using matching colors for corresponding objects.
Setting Up Data spaces in GeoServer
After completing the initial platform setup (refer to the Admin Guide), GeoServer is automatically configured to synchronize roles from Keycloak, ensuring it recognizes all existing platform roles (for each data space).
During each user login, their assigned roles are also synced with GeoServer. The only remaining manual step is to assign the appropriate permissions to these synced roles at the workspace level. Once this is done, permissions are validated each time a user requests access to any content.
For further details on GeoServer administration, please consult the Admin Guide.